Your Stride threat model example images are ready. Stride threat model example are a topic that is being searched for and liked by netizens today. You can Download the Stride threat model example files here. Find and Download all royalty-free vectors.
If you’re looking for stride threat model example pictures information connected with to the stride threat model example keyword, you have come to the ideal site. Our website frequently gives you hints for downloading the highest quality video and image content, please kindly hunt and find more informative video content and graphics that fit your interests.
Stride Threat Model Example. What is a Threat Model. It allows software architects to identify and mitigate potential security issues early when they are relatively easy and cost-effective to resolve. Here is the obligatory Wikipedia definition. Trike is a threat modeling framework with similarities to the Microsoft threat modeling processes.
 Strike With The S T R I D E Threat Modelling By Praveen Anushka Medium From medium.com
Strike With The S T R I D E Threat Modelling By Praveen Anushka Medium From medium.com
Trike is a threat modeling framework with similarities to the Microsoft threat modeling processes. Invented in 1999 and adopted by Microsoft in 2002 STRIDE is currently the most mature threat-modeling method. Can be used You need a very complete list but you can combine threats that are common. Our main contribution is a STRIDE threat model that is offered solely in the context of 5G core slicing. It models the in-place system. His recent posts are Threat Modeling Once Again Threat modeling again.
Threat modeling provides security teams with a practical framework for dealing with a threat.
Applying STRIDE-per-element to the diagram shown in Figure E-1 Acme would rank the threats with a bug bar although because neither the bar nor the result of such ranking is critical to this example they are not shown. Once you get used to applying the STRIDE model it often boils down to getting the DFD right brainstorming attacks and reviewing the known checklists. In this article I offer a high-level introduction to one methodology called STRIDE and in a future article I will demonstrate this process using an existing open-source application as an example. STRIDE has evolved over time to include new threat-specific tables and the variants STRIDE-per-Element and STRIDE-per-Interaction. Threat Modeling also called Architectural Risk Analysis is an essential step in the development of your application. Our main contribution is a STRIDE threat model that is offered solely in the context of 5G core slicing.
 Source: resources.infosecinstitute.com
Source: resources.infosecinstitute.com
Threat modeling provides security teams with a practical framework for dealing with a threat. STRIDEs threat model accounts for six different threat categories. TD is both a web application and a desktop application. STRIDE has evolved over time to include new threat-specific tables and the variants STRIDE-per-Element and STRIDE-per-Interaction. Threat Modeling Using STRIDE.
 Source: researchgate.net
Source: researchgate.net
Can be used You need a very complete list but you can combine threats that are common. Threat Ratings 19 Use of Threat-Model 19 Rating Priority High Medium Low 19 Using STRIDE-Model for Classification of Threats 20 Using DREAD-Model for Rating Risk 21 Procedure for DREAD-Model Risk Analysis 22 Conclusion 23 1. His recent posts are Threat Modeling Once Again Threat modeling again. Threat Property Definition Example Information Disclosure Confidentiality Exposing information to. Threat Modeling Example 13.
 Source: securecav.com
Source: securecav.com
Threat Modeling Example 13. His recent posts are Threat Modeling Once Again Threat modeling again. It models the in-place system. Threat Modeling as a structured activity for identifying and managing the objects such as application threats. Can be used You need a very complete list but you can combine threats that are common.
 Source: insights.sei.cmu.edu
Source: insights.sei.cmu.edu
Hes been a threat modeling advocate for years and has been blogging a lot about our new processes and describes in great detail the STRIDE per element process. Trike is a threat modeling framework with similarities to the Microsoft threat modeling processes. It allows software architects to identify and mitigate potential security issues early when they are relatively easy and cost-effective to resolve. STRIDE and Associated Derivations. Step 1 - Identify Security Objectives - Provide an environment.
 Source: researchgate.net
Source: researchgate.net
His recent posts are Threat Modeling Once Again Threat modeling again. Consider the system that provides web access to your bank account. Example of a STRIDE Threat Model. Threat Modeling Using STRIDE By. Threat Modeling Using STRIDE.
 Source: online.visual-paradigm.com
Source: online.visual-paradigm.com
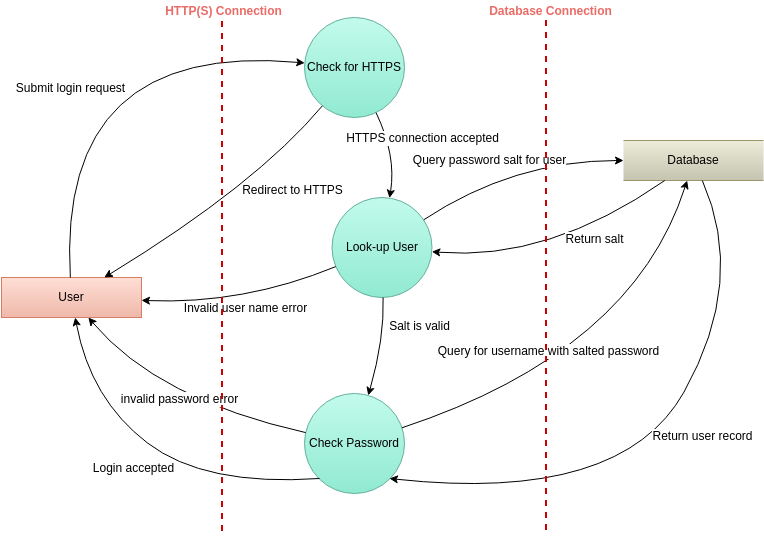
Threat Modeling Using STRIDE. Girindro Pringgo Digdo MT CSX-F. Visual Paradigm Online VP Online an online Threat Model Diagram drawing editor that supports Threat Model Diagram and other diagram types such as ERD Organization Chart and more. Okay lets look at an example. However Trike differs because it uses a risk based approach with distinct implementation threat and risk models instead of using the STRIDEDREAD aggregated threat model attacks threats and weaknesses.
 Source: xebia.com
Source: xebia.com
Mallory sends a letter to Ben and signs Alice wrote this. Our main contribution is a STRIDE threat model that is offered solely in the context of 5G core slicing. Once you get used to applying the STRIDE model it often boils down to getting the DFD right brainstorming attacks and reviewing the known checklists. Hes been a threat modeling advocate for years and has been blogging a lot about our new processes and describes in great detail the STRIDE per element process. Some threats are listed by.
 Source: dzone.com
Source: dzone.com
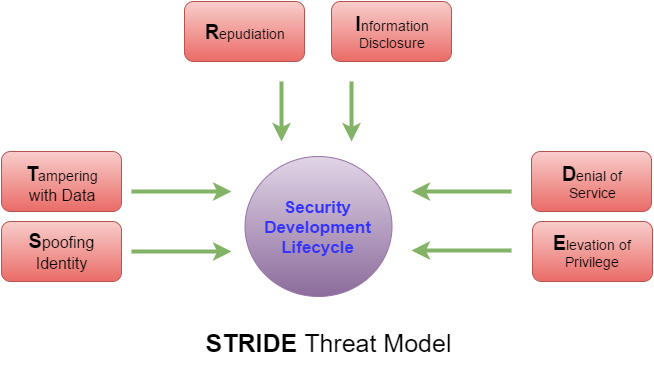
STRIDEs threat model accounts for six different threat categories. Mallory sends a letter to Ben and signs Alice wrote this. For example the STRIDE model offers a proven methodology of next steps. Identify spoofing occurs when the hacker pretends to be another person assuming the identity and information in that identity to commit fraud. With the intuitive Threat Model Diagram editor you can draw Threat Model Diagram in seconds.
 Source: researchgate.net
Source: researchgate.net
Threat Ratings 19 Use of Threat-Model 19 Rating Priority High Medium Low 19 Using STRIDE-Model for Classification of Threats 20 Using DREAD-Model for Rating Risk 21 Procedure for DREAD-Model Risk Analysis 22 Conclusion 23 1. Identify spoofing occurs when the hacker pretends to be another person assuming the identity and information in that identity to commit fraud. Note that the following types of threats are excluded from our model. What is a Threat Model. Threat Modeling Using STRIDE By.
 Source: youtube.com
Source: youtube.com
Identify spoofing occurs when the hacker pretends to be another person assuming the identity and information in that identity to commit fraud. Threat Modeling as a structured activity for identifying and managing the objects such as application threats. As a result it greatly reduces the total cost of development. Our main contribution is a STRIDE threat model that is offered solely in the context of 5G core slicing. Threat modeling provides security teams with a practical framework for dealing with a threat.
 Source: online.visual-paradigm.com
Source: online.visual-paradigm.com
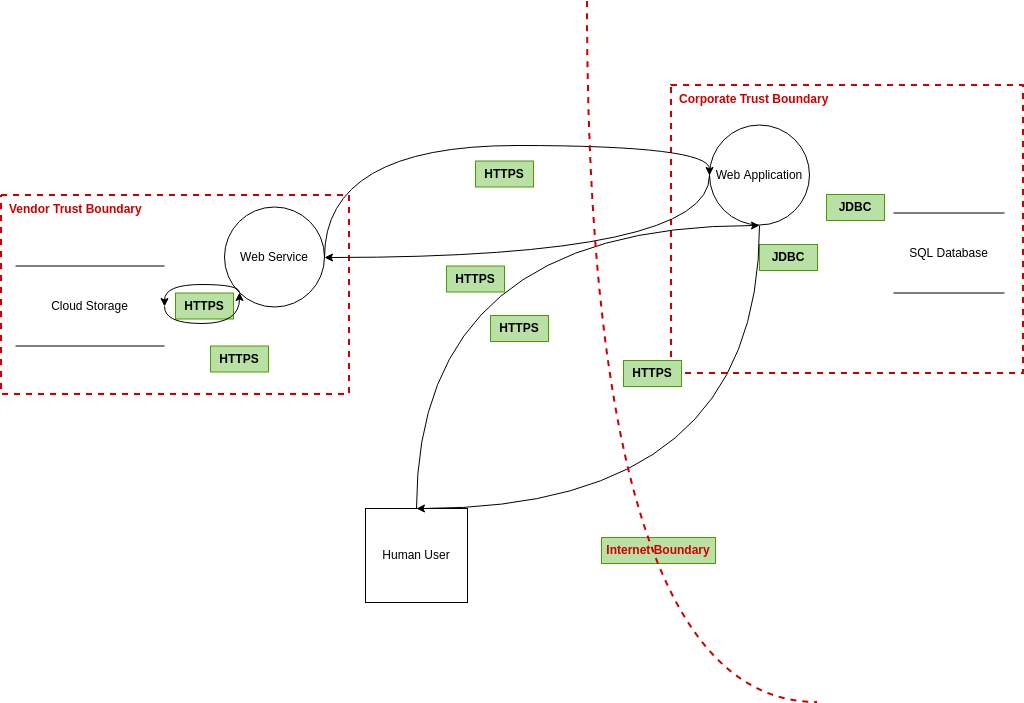
Threat Modeling Using STRIDE. Trike is a threat modeling framework with similarities to the Microsoft threat modeling processes. TD is both a web application and a desktop application. Note that the following types of threats are excluded from our model. STRIDE separates things that can go wrong in six categories.
 Source: debiotech.com
Source: debiotech.com
It allows software architects to identify and mitigate potential security issues early when they are relatively easy and cost-effective to resolve. Invented in 1999 and adopted by Microsoft in 2002 STRIDE is currently the most mature threat-modeling method. As a result it greatly reduces the total cost of development. It allows software architects to identify and mitigate potential security issues early when they are relatively easy and cost-effective to resolve. One such security practice is Threat Modeling.

Example of a STRIDE Threat Model. Consider the system that provides web access to your bank account. As a result it greatly reduces the total cost of development. Trike is a threat modeling framework with similarities to the Microsoft threat modeling processes. Identify spoofing occurs when the hacker pretends to be another person assuming the identity and information in that identity to commit fraud.
 Source: softwaresecured.com
Source: softwaresecured.com
Our main contribution is a STRIDE threat model that is offered solely in the context of 5G core slicing. Refer to the projects GitHub repository for the latest release. It models the in-place system. For example the STRIDE model offers a proven methodology of next steps. Threat Modeling Example 13.
 Source: researchgate.net
Source: researchgate.net
Threat modeling provides security teams with a practical framework for dealing with a threat. Girindro Pringgo Digdo MT CSX-F. It allows software architects to identify and mitigate potential security issues early when they are relatively easy and cost-effective to resolve. Here is the obligatory Wikipedia definition. Threat Modeling Example 13.
 Source: docs.microsoft.com
Source: docs.microsoft.com
Threat model and document The product as a whole The security-relevant features. Applying STRIDE-per-element to the diagram shown in Figure E-1 Acme would rank the threats with a bug bar although because neither the bar nor the result of such ranking is critical to this example they are not shown. Invented in 1999 and adopted by Microsoft in 2002 STRIDE is currently the most mature threat-modeling method. Threat modeling provides security teams with a practical framework for dealing with a threat. It allows software architects to identify and mitigate potential security issues early when they are relatively easy and cost-effective to resolve.
 Source: medium.com
Source: medium.com
TD is both a web application and a desktop application. As you strive to develop secure software we recommend threat modeling as a key part of your process and specifically the STRIDE model presented in this article. Can be used You need a very complete list but you can combine threats that are common. Invented in 1999 and adopted by Microsoft in 2002 STRIDE is currently the most mature threat-modeling method. Hes been a threat modeling advocate for years and has been blogging a lot about our new processes and describes in great detail the STRIDE per element process.
 Source: semanticscholar.org
Source: semanticscholar.org
Note that the following types of threats are excluded from our model. Invented in 1999 and adopted by Microsoft in 2002 STRIDE is currently the most mature threat-modeling method. STRIDE and Associated Derivations. Consider the system that provides web access to your bank account. Threat Property Definition Example Information Disclosure Confidentiality Exposing information to.
This site is an open community for users to share their favorite wallpapers on the internet, all images or pictures in this website are for personal wallpaper use only, it is stricly prohibited to use this wallpaper for commercial purposes, if you are the author and find this image is shared without your permission, please kindly raise a DMCA report to Us.
If you find this site convienient, please support us by sharing this posts to your favorite social media accounts like Facebook, Instagram and so on or you can also bookmark this blog page with the title stride threat model example by using Ctrl + D for devices a laptop with a Windows operating system or Command + D for laptops with an Apple operating system. If you use a smartphone, you can also use the drawer menu of the browser you are using. Whether it’s a Windows, Mac, iOS or Android operating system, you will still be able to bookmark this website.






