Your Second line of defense examples images are available in this site. Second line of defense examples are a topic that is being searched for and liked by netizens today. You can Get the Second line of defense examples files here. Find and Download all free images.
If you’re looking for second line of defense examples images information linked to the second line of defense examples interest, you have visit the right blog. Our site frequently gives you suggestions for seeing the highest quality video and image content, please kindly hunt and locate more informative video articles and images that match your interests.
Second Line Of Defense Examples. Barriers at the Portal of Entry. Second Line of Defense. It is a 3-pronged attack on any microbes that have survived the first line of defence. The second line of defence involves specialist cells and white blood cells such as phagotcytes macrophages neutrophils natural killer cells dendritic.
 Lines Of Defense Bioninja From ib.bioninja.com.au
Lines Of Defense Bioninja From ib.bioninja.com.au
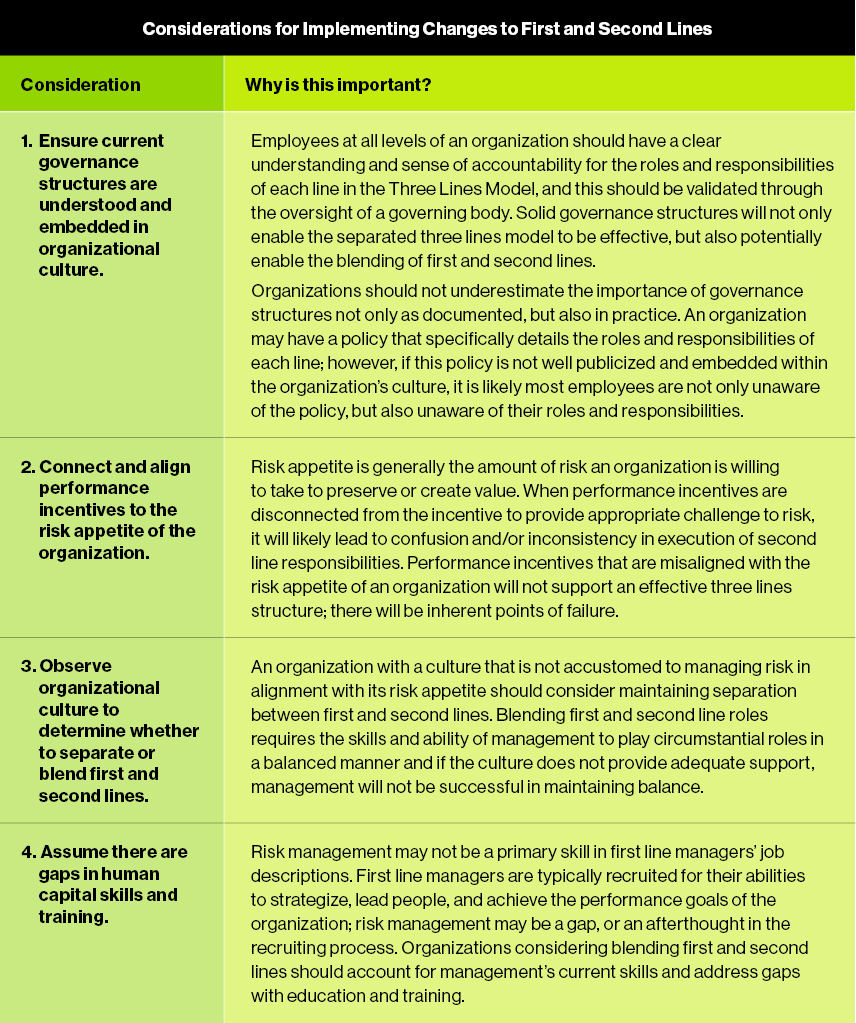
The second line of defense is put in place to support senior management by bringing expertise and monitoring alongside the first line to ensure that risks and controls are properly managed. Helping prevent spread of infection. In this imperfect world the second line serves a very important role and purposesupporting the first line of defense. The specific functions will vary by organisation industry size and risk of the project but typical functions in this second line of defence are outlined in Table 1. The second line of defence. Phagocytic cells ingest and destroy all microbes that pass into body tissues.
Barriers at the Portal of Entry.
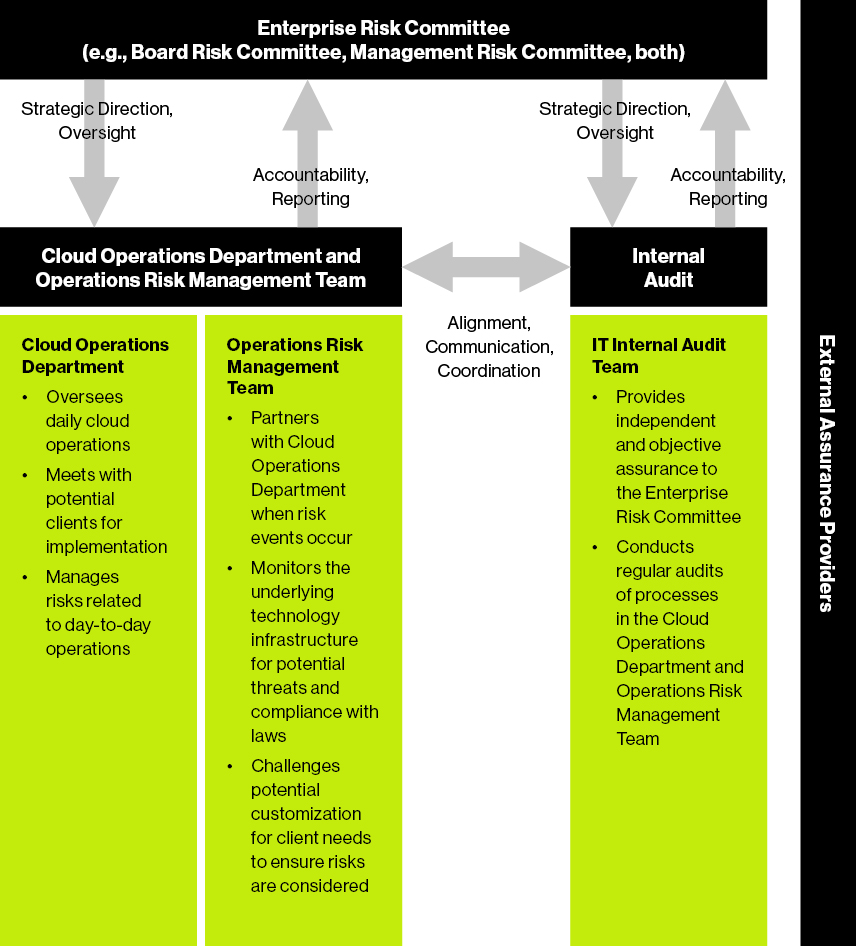
1 Chapter 14 Topics - Defense Mechanisms - Non-specific immunity Defense Mechanisms Innate - Non specific First line of defense Second line of defense Acquired - Specific Third line of defense Summary of the major components of the host defenses. Second Line of Defense. The third line is comprised of independent assurance providers. Visibility through dashboards The compliance functions monitoring tasks are split between those it undertakes itself and those carried out by others under its oversight. Expand the customer base. 2nd Line of Defense Examples Compliance Legal Financial control Security Risk management Quality Health and safety Inspection Environmental Supply chain 24.
 Source: khanacademy.org
Source: khanacademy.org
The specific functions will vary by organisation industry size and risk of the project but typical functions in this second line of defence are outlined in Table 1. Dilate this is known as edema. Essentially this is a management and oversight function that owns aspects of the risk management process. The second line of defence involves specialist cells and white blood cells such as phagotcytes macrophages neutrophils natural killer cells dendritic. A response to a pathogen regardless of its type.
 Source: youtube.com
Source: youtube.com
These defense mechanisms destroy invaders in a general way and do not target specific antigens. The second line of defence takes action when the first line of defence has failed. The specific functions will vary by organisation industry size and risk of the project but typical functions in this second line of defence are outlined in Table 1. Essential to effective risk management the lines-of-defense model is implicit in COSOs internal control framework through the control environment control activities monitoring and other components of an internal control system. Expand the customer base.
 Source: guidehouse.com
Source: guidehouse.com
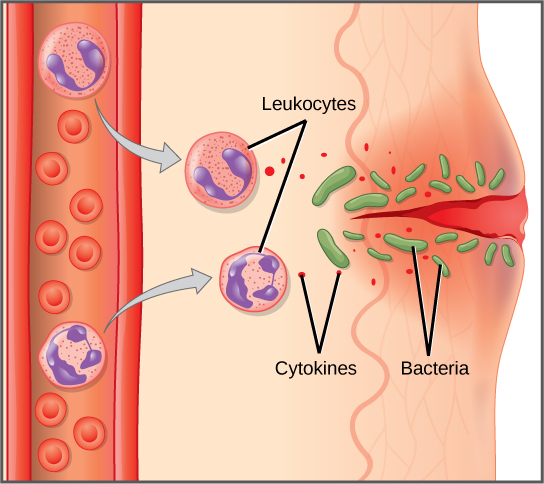
The second line of defense oversees the controls implemented by the first line of defense and performs routine monitoring of the risk. Macrophages leave the bloodstream and enter. Here we understand the second line of defense in a simplified structured manner. Inflammation Yes this is good Inflammation happens because cells damaged by invading pathogens and particular white blood cells release alarm chemicals which makes. If you have a cut on your hand the break in the skin provides a way for pathogens to enter your body.
 Source: guidehouse.com
Source: guidehouse.com
Inflammation Yes this is good Inflammation happens because cells damaged by invading pathogens and particular white blood cells release alarm chemicals which makes. For example macrophages are cells derived from monocytes a type of white blood cell. The Second Line of Defense. Second Line of Defence is innate form of non specific defense that removes pathogen entered into the body after bypassing first line of defense by means of defensive cells proteins fever and inflammation. The second line of defense is put in place to support senior management by bringing expertise and monitoring alongside the first line to ensure that risks and controls are properly managed.
 Source: guidehouse.com
Source: guidehouse.com
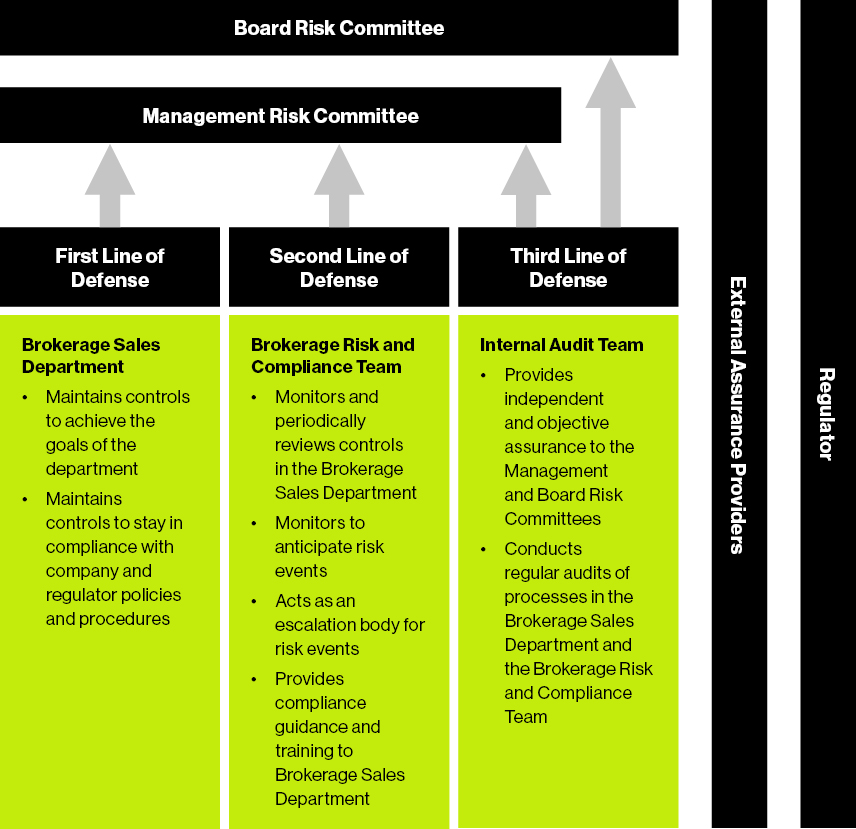
WBCs microbes debris and fluid collect to form pus. Natural Killer NK cells. Visibility through dashboards The compliance functions monitoring tasks are split between those it undertakes itself and those carried out by others under its oversight. Barriers at the Portal of Entry. The second line is comprised of the standard setters or risk oversight groups eg compliance functions legal and enterprise risk management which are responsible for establishing policies and procedures and serving as the management oversight over the first line the doers.
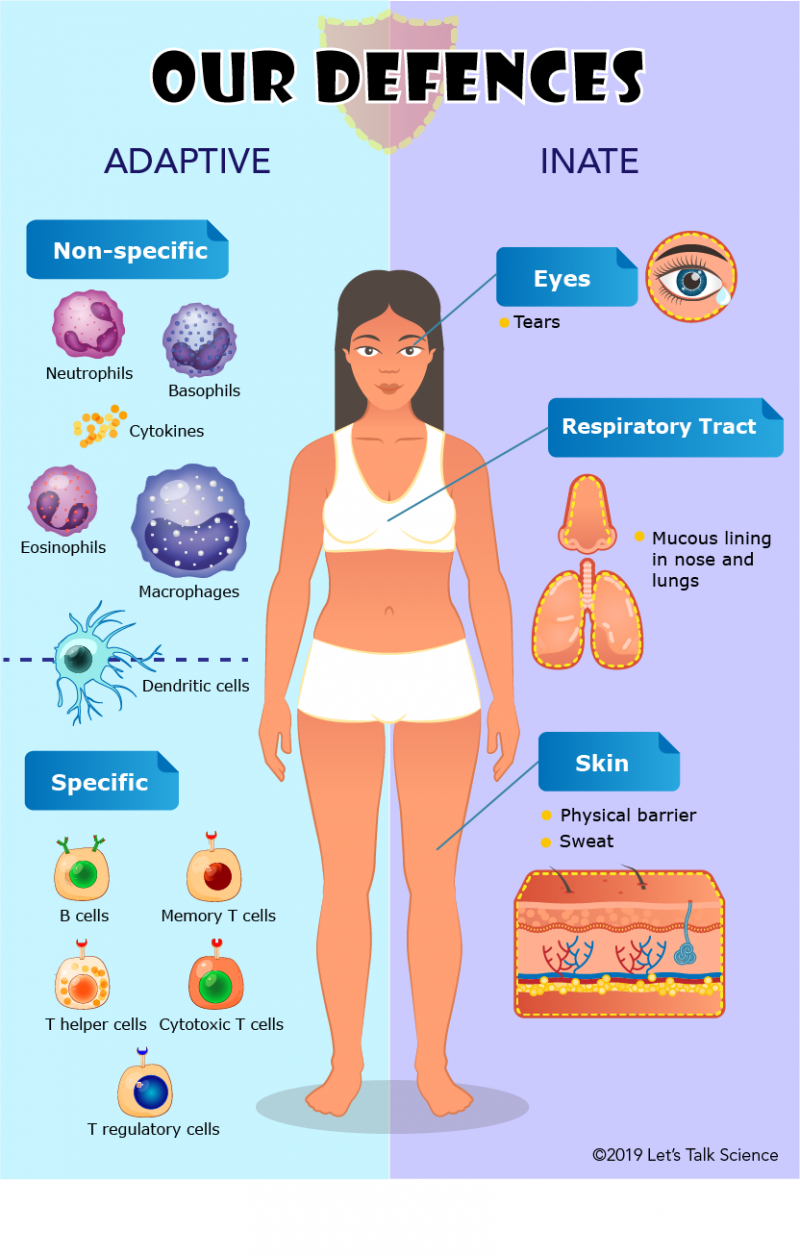 Source: letstalkscience.ca
Source: letstalkscience.ca
Third line of defence which includes monitoring the compliance function. 2nd Line of Defense The 2nd LoD is also called as the Risk Monitoring and Oversight. The response is the same for any pathogen. It is comprised of phagocytosis fever inflammation interferon production and the. WBCs microbes debris and fluid collect to form pus.
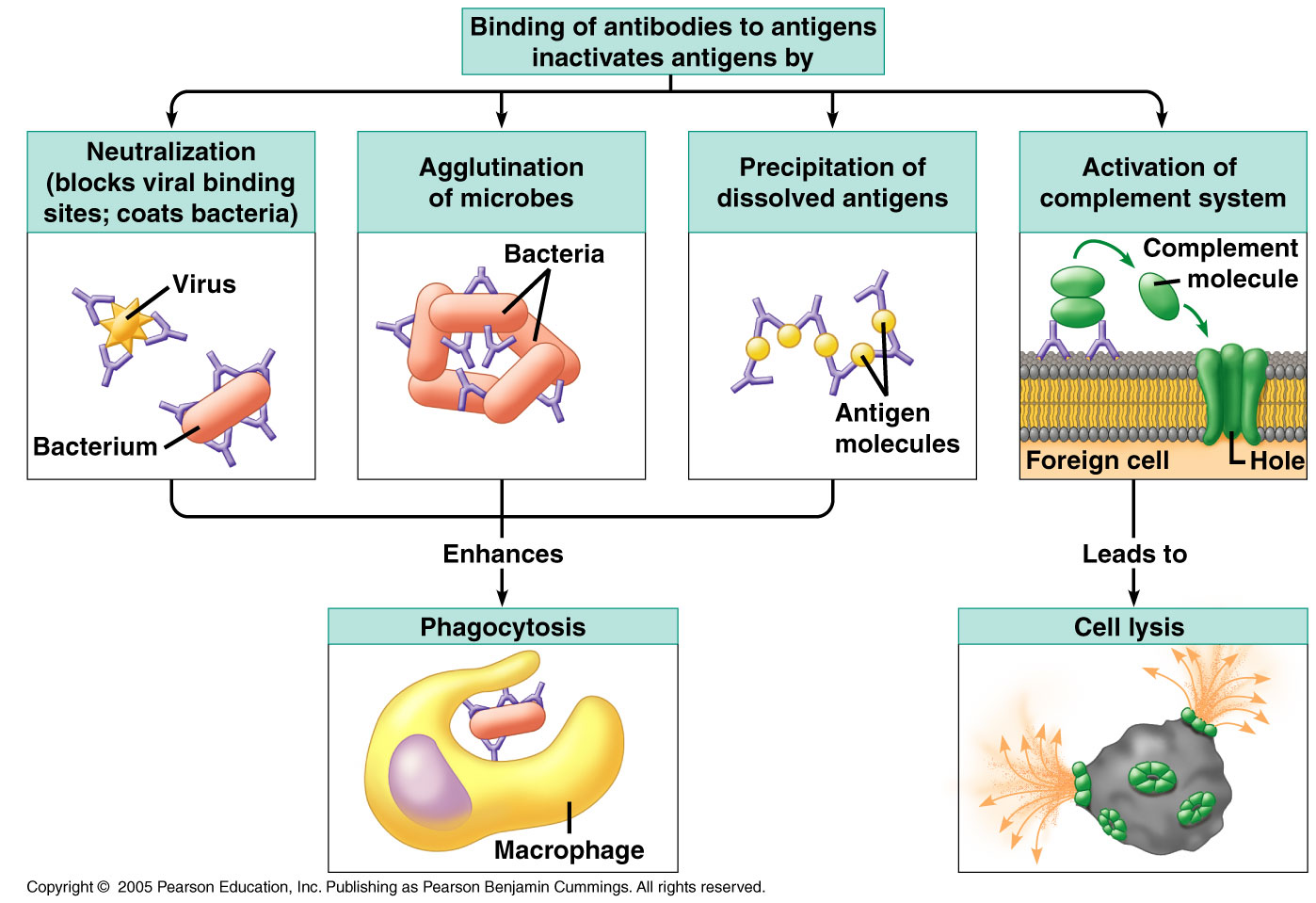 Source: austincc.edu
Source: austincc.edu
Essentially this is a management and oversight function that owns aspects of the risk management process. 1 Chapter 14 Topics - Defense Mechanisms - Non-specific immunity Defense Mechanisms Innate - Non specific First line of defense Second line of defense Acquired - Specific Third line of defense Summary of the major components of the host defenses. They get past the first line of defense and run into the second line of defense. If you have a cut on your hand the break in the skin provides a way for pathogens to enter your body. Essentially this is a management and oversight function that owns aspects of the risk management process.
 Source: www2.erm-academy.org
Source: www2.erm-academy.org
WBCs microbes debris and fluid collect to form pus. Thus it provides both the fi rst and second line of defence in terms of different compliance risks. The Second Line of Defense. It involves structures of the body. Another name for the First Line of defense is.
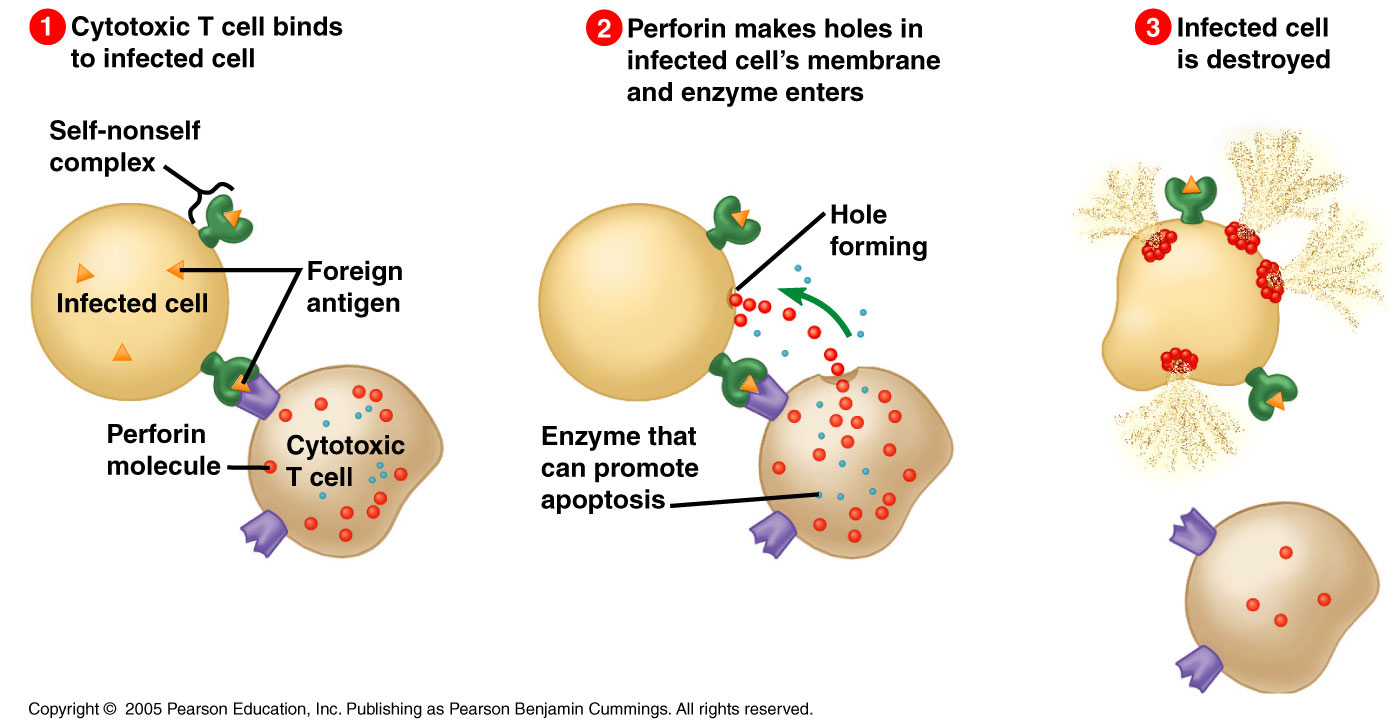 Source: austincc.edu
Source: austincc.edu
Second Line of Defense. Swelling Increased fluid escaping into the tissue as bv. The second line of defense is _____ Innate and nonspecific. It is comprised of phagocytosis fever inflammation interferon production and the. It involves structures of the body.
 Source: ib.bioninja.com.au
Source: ib.bioninja.com.au
The second line of defense is put in place to support senior management by bringing expertise and monitoring alongside the first line to ensure that risks and controls are properly managed. Second Line of Defence is innate form of non specific defense that removes pathogen entered into the body after bypassing first line of defense by means of defensive cells proteins fever and inflammation. Another name for the First Line of defense is. Inflammation Yes this is good Inflammation happens because cells damaged by invading pathogens and particular white blood cells release alarm chemicals which makes. The second line of defense is the independent control function eg IT risk IT compliance that oversees risk and monitors the first-line-of-defense controls.
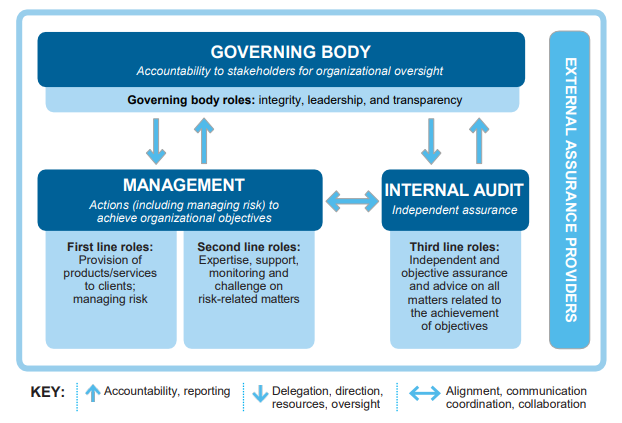 Source: internalaudit.olemiss.edu
Source: internalaudit.olemiss.edu
The Information Security and Risk Management typically resides in the 2nd LoD. The second line of defense of the immune system also an aspect of innate immunity is the nonspecific resistance. The second line of defense is nonspecific resistance that destroys invaders in a generalized way without targeting specific individuals. The second line of defense is put in place to support senior management by bringing expertise and monitoring alongside the first line to ensure that risks and controls are properly managed. 13 3rd Line of Defense Internal Audit has been clearly defined as the Third Line.
 Source: icas.com
Source: icas.com
The second line of defense is put in place to support senior management by bringing expertise and monitoring alongside the first line to ensure that risks and controls are properly managed. The third line is comprised of independent assurance providers. Here we understand the second line of defense in a simplified structured manner. For example macrophages are cells derived from monocytes a type of white blood cell. Phagocytes Phagocytic cells ingest and destroy microbes that pass into body tissues.
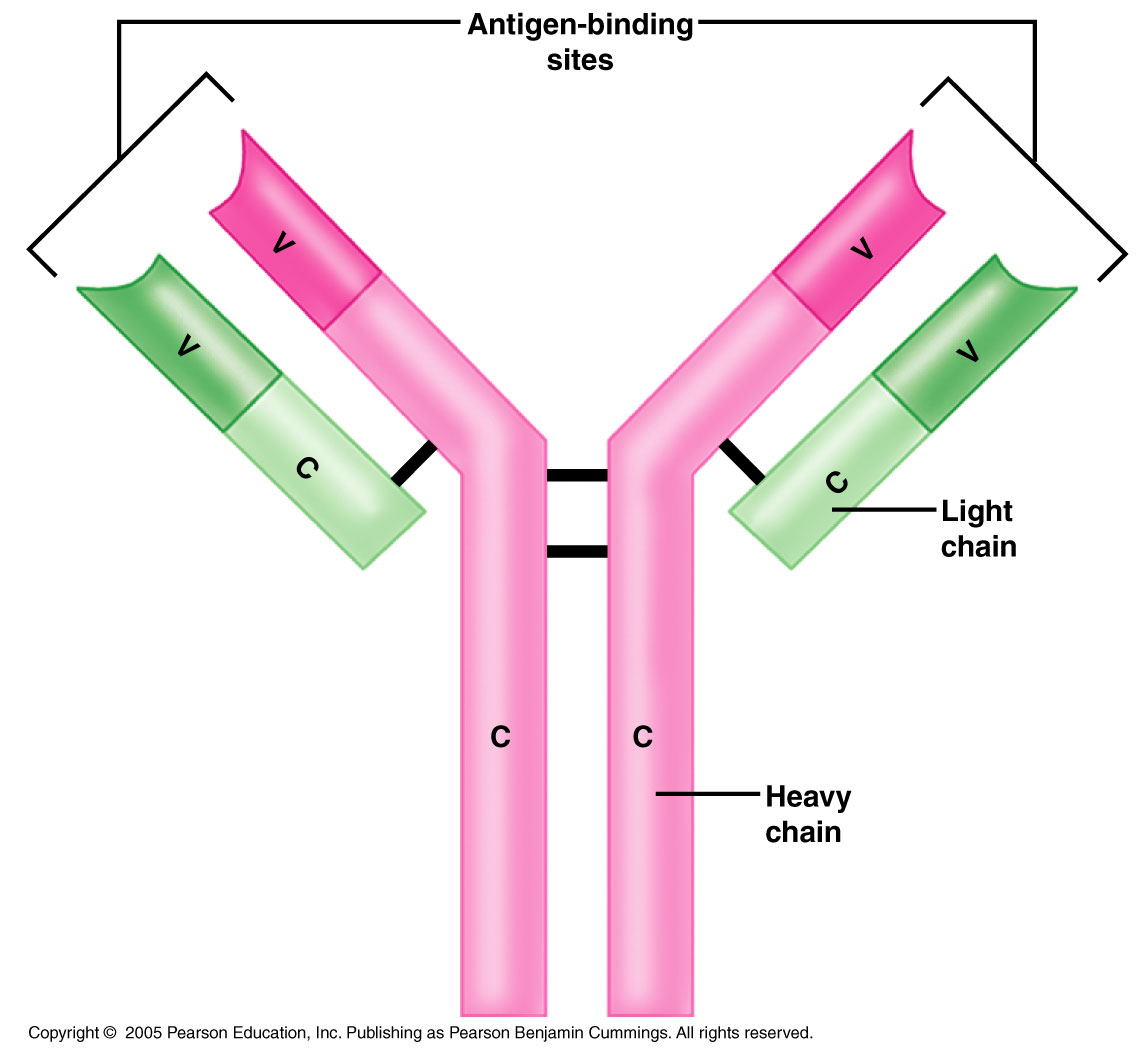 Source: austincc.edu
Source: austincc.edu
2nd Line of Defense The 2nd LoD is also called as the Risk Monitoring and Oversight. Second Line of Defence is innate form of non specific defense that removes pathogen entered into the body after bypassing first line of defense by means of defensive cells proteins fever and inflammation. Essential to effective risk management the lines-of-defense model is implicit in COSOs internal control framework through the control environment control activities monitoring and other components of an internal control system. The third line of defense is internal audit which provides independent assurance. Is an example of Internal Defense.
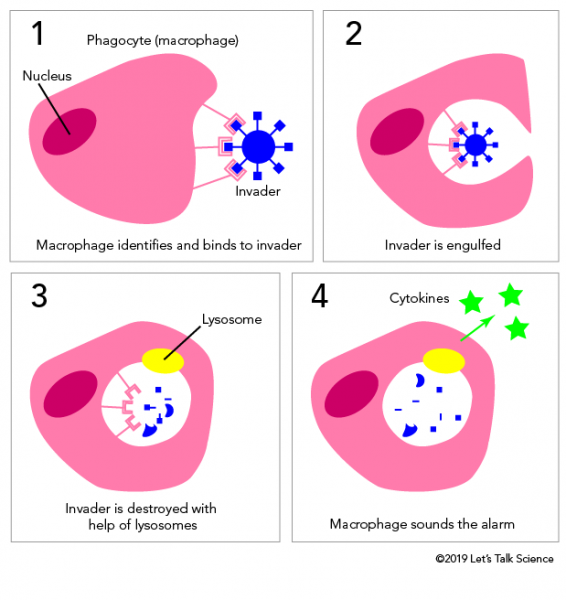 Source: letstalkscience.ca
Source: letstalkscience.ca
The specific functions will vary by organisation industry size and risk of the project but typical functions in this second line of defence are outlined in Table 1. Helping prevent spread of infection. Phagocytic cells ingest and destroy all microbes that pass into body tissues. The Second Line of Defense. If you have a cut on your hand the break in the skin provides a way for pathogens to enter your body.
 Source: youtube.com
Source: youtube.com
Phagocytes Phagocytic cells ingest and destroy microbes that pass into body tissues. Natural Killer NK cells. Barriers at the Portal of Entry. The second line of defence involves specialist cells and white blood cells such as phagotcytes macrophages neutrophils natural killer cells dendritic. The second line of defense is _____ Innate and nonspecific.
 Source: guidehouse.com
Source: guidehouse.com
The second line of defence provides subject matter expertise through a facilitation or support role to assist the first line in project risk management. Assume bacteria enter through the cut and infect the wound. The second line is comprised of the standard setters or risk oversight groups eg compliance functions legal and enterprise risk management which are responsible for establishing policies and procedures and serving as the management oversight over the first line the doers. Barriers at the Portal of Entry. Macrophages leave the bloodstream and enter.
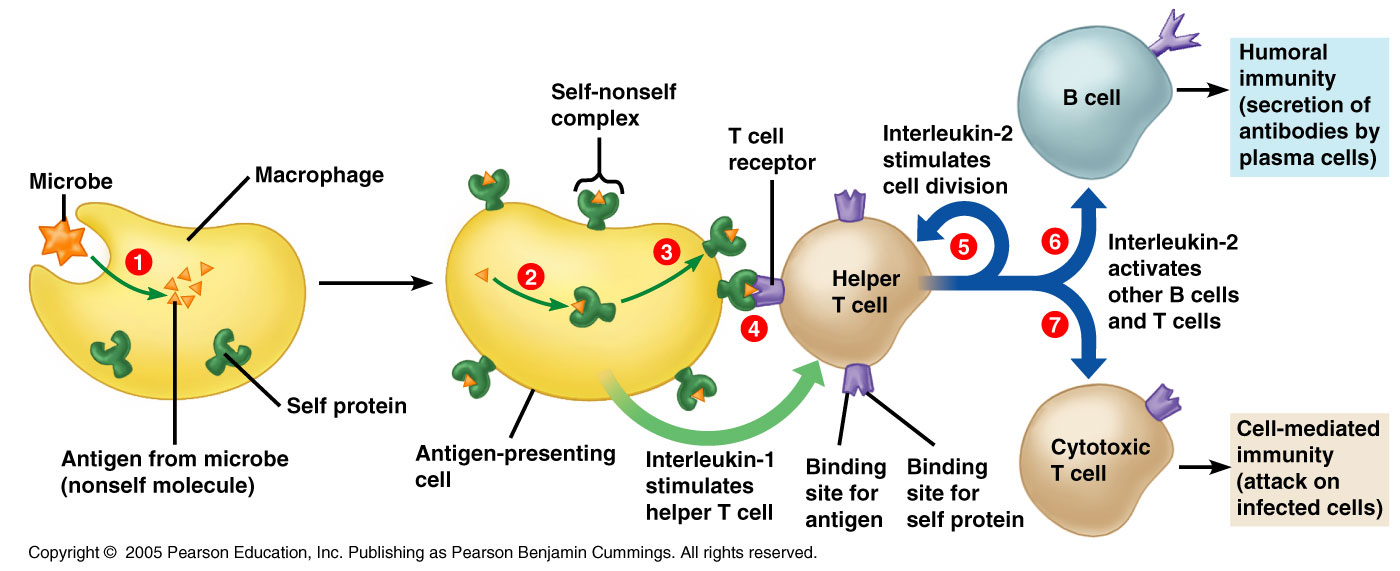 Source: austincc.edu
Source: austincc.edu
The second line of defence takes action when the first line of defence has failed. It can challenge the effectiveness of controls and management of risk across the organization. It is a 3-pronged attack on any microbes that have survived the first line of defence. Is an example of Internal Defense. The second line of defence provides subject matter expertise through a facilitation or support role to assist the first line in project risk management.
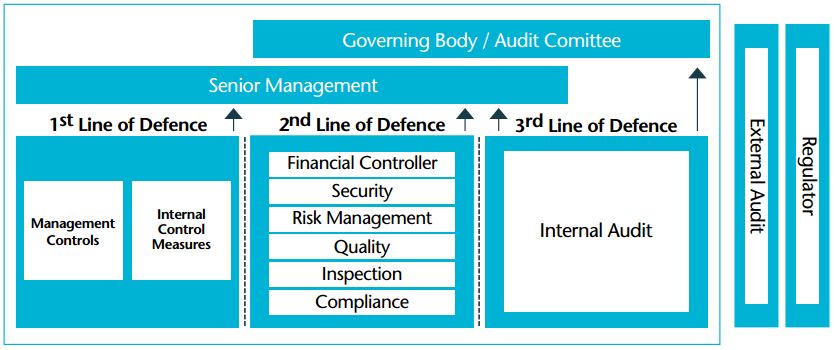 Source: icas.com
Source: icas.com
The Second Line of Defense. A response to a pathogen regardless of its type. 1 Chapter 14 Topics - Defense Mechanisms - Non-specific immunity Defense Mechanisms Innate - Non specific First line of defense Second line of defense Acquired - Specific Third line of defense Summary of the major components of the host defenses. If you have a cut on your hand the break in the skin provides a way for pathogens to enter your body. Second Line of Defence is innate form of non specific defense that removes pathogen entered into the body after bypassing first line of defense by means of defensive cells proteins fever and inflammation.
This site is an open community for users to do submittion their favorite wallpapers on the internet, all images or pictures in this website are for personal wallpaper use only, it is stricly prohibited to use this wallpaper for commercial purposes, if you are the author and find this image is shared without your permission, please kindly raise a DMCA report to Us.
If you find this site helpful, please support us by sharing this posts to your favorite social media accounts like Facebook, Instagram and so on or you can also bookmark this blog page with the title second line of defense examples by using Ctrl + D for devices a laptop with a Windows operating system or Command + D for laptops with an Apple operating system. If you use a smartphone, you can also use the drawer menu of the browser you are using. Whether it’s a Windows, Mac, iOS or Android operating system, you will still be able to bookmark this website.






